Data protection policy
Introduction
Data plays a fundamental part in delivering the charity’s objectives. Re-engage collects and processes personal data of vulnerable service users (older people), volunteers, donors, and supporters, staff, and trustees, and creates confidential business information. It is a legal requirement to demonstrate appropriate and effective compliance with data protection regulation, as set out in data protection and privacy laws of the UK and Crown Dependencies.
Aim
This policy ensures data is collected and handled in a lawful and ethical manner. It introduces a system of accountability based on job roles, and ensuring privacy and data protection are considered from the start of any project and then regularly reviewed.
This policy is complemented by appendices of supporting processes that may be updated to meet the requirements of the policy.
By adhering to this policy, and supporting processes, we show that we can be trusted to use data in line with legal requirements.
Scope
This policy applies to:
- Information systems that collect, store, process, disseminate, transmit, or dispose of information; including third-party information systems that connect to Re-engage systems. Information systems that may be entirely paper-based, computer based, or a combination of both; an information system is a system that incorporates all the processes needed to effectively manage data.
- Information assets includes personal and sensitive data about individuals and / or confidential data of the charity's official activities; wherever collected, stored, used, accessed, shared, transported, retained, or deleted.
Audience, roles, and responsibilities
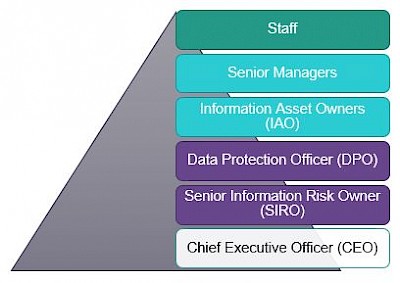
Some positions may be held by the same individual, and some may be held by more than one individual if there is a clear segregation of duties.
Colleagues
Controls, processes, and mitigations arising from this policy apply to all charity employees, trustees, freelancers, interns, and volunteers who operate or have access to any information asset (data or system) controlled by Re-engage. All colleagues share in a collective responsibility to ensure:
- Information is processed, stored, and transmitted in ways that data subjects (such as an older person, volunteer, or supporter) may reasonably expect from what they were told when they provided us with the information; and that procedures, standards, and protocols to protect information assets are observed.
- There is no intentional compromise of any data protection measures put in place by the charity; and that there is no personal activity that results in, or causes risk to, the security of the information the charity holds.
- That colleagues promptly report any concern, suspected risk, near miss, or accidental or unlawful disclosure of restricted information in accordance with our reporting procedure and take part in remedial action only when instructed.
Information asset owner(s) (IAO) and senior managers
The role of IAO typically applies to members of the leadership team but may also be assigned or shared with persons responsible for oversight of an initiative (service, project, or plan) that introduces, procures, modifies, or operates information assets (data or systems).
IAOs are accountable for ensuring that information systems under their control – and the colleagues that use them – operate in compliance with this policy and related laws. IAOs have a thorough understanding of this policy and management processes.
In practice, it is the responsibility of the leadership team and IAOs to practice a higher level of vigilance in relation to data protection risks, undertake screening processes to determine actions, and use Data Protection Impact Assessments (DPIAs) in relation to their information assets. IAOs also lead in internally reporting, investigating, and coordinating responses to incidents and privacy breaches.
Data Protection Officer (DPO)
The DPO monitors internal compliance with data protection legislation, data protection policies and statements, awareness-raising, training, and audits. The DPO reports directly to our CEO and is given the required independence and resources to perform their tasks. We involve our DPO, in a timely manner, in all issues relating to the protection of personal data. When carrying out a Data Protection Impact Assessment (DPIA), we seek the advice of our DPO who also monitors the process. We do not penalise the DPO for performing their duties and ensure that any other tasks or duties we assign to our DPO do not result in a conflict of interests with their role as a DPO.
The DPO is responsible for investigating, externally reporting, and coordinating responses to concerns and incidents. They are registered with the ICO (and Crown Dependency equivalents) as an official point of contact regarding data protection at Re-engage, and their contact details are also published in our public privacy policy.
Responsibility
The board of trustees is ultimately responsible for data protection and delegates this to the Chief Executive (CEO) at Re-engage. The CEO delegates this responsibility to the Data Protection Officer (DPO). The CEO, senior leadership team (SLT) and senior management team (SMT) are responsible for allocating resources and fostering commitment to data protection across the charity.
Third party suppliers
Partner organisations and third parties involved in provision of services contribute the necessary technical information for Data Protection Impact Assessments (DPIAs), as well as data protection assurance and notifications of breaches or incidents. It is the responsibility of IAOs and the DPO to ensure suppliers’ adhere to this policy
Support and training
Re-engage requires all staff to complete, and periodically renew, training on data protection and information security. Senior managers will also promote, support, and refer staff to processes arising from this policy as needed.
Definitions and principles of data protection
The key definitions and principles discussed in this policy are available online by visiting the Information Commissioner's Office (ICO). Additional guidance and information about data protection regulations can be found by visiting the ICO website.
Types of protected data
Personal data
Legislation defines personal data as:
“any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person”
Personal data can be factual information about a person (for example, their name, address, or date of birth). It can also be an opinion about that person, their actions, or behaviour. Data can still be personal data even if it – on its own – does not identify a living individual. A document including a persons’ OPUS ID (CON number) rather than their name, for example, would still be personal data, because other information which we hold would allow us to identify the individual.
The individual that personal data relates to is called the ‘data subject.’ Data subjects have clearly defined rights about how we process their data. (See legal principles and rights of individuals).
Sensitive personal data
Some types of personal data – being more sensitive in nature – merit additional protection as disclosure of such data may cause a person to be treated unfairly or in a prejudicial way. Sensitive personal data is any data about an individual which falls into the following categories:
- their racial or ethnic origin
- their political opinions
- their religious beliefs
- their membership of a trade union
- their physical or mental health or condition
- their sexual life
- any actual or alleged criminal offence
- any court proceedings / sentences
Even if personal data does not fall within any of these categories, additional measures to collect and process personal data may be necessary if it relates to a vulnerable person, or where inappropriate disclosure would cause damage and distress to the data subjects.
Re-engage has a legal - and moral - responsibility to ensure data supplied in confidence is never disclosed to anyone else without the data subject’s explicit and affirmative consent. Data may be disclosed without consent where there is a legal requirement for us to do so e.g., law-enforcement purposes, or to safeguard a child or vulnerable adult). Any inappropriate disclosure of personal data is unacceptable and may result in disciplinary action. Deliberately accessing or disclosing personal data without authority may also constitute a criminal offence and may result in prosecution.
Confidential information about Re-engage’s activities
Confidential information should also be protected and includes any information about Re-engage that if disclosed may be:
- Prejudicial to the activities of the charity.
- Could be used to threaten the security of its property and its systems; or
- Could cause embarrassment to the organisation, including any documents that include:
- Commercially sensitive data about the charity; procurements, contracts, sponsorship information, or non-public details about the charity’s finances.
- Internal management discussions or decisions not for current disclosure such as project planning and risk information.
- Information security arrangements; login details, details on physical and remote access to servers.
Confidential information about Re-engage’s activities must not be disclosed unless there is a legitimate reason for doing so. Disclosing confidential information about Re-engage’s activities without a legitimate reason and / or senior-level approval may result in disciplinary action.
Legal principles and rights of individuals
Data Protection legislation sets out guidelines for data controllers to follow regarding the use of data and the rights of individuals concerning their data. Re-engage is dedicated to implementing these principles in all activities involving protected data by adhering to the following:
Processed fairly and lawfully
Only processing personal and sensitive data where:
- Processing does not have negative effects on the data subject
- Methods and implications of processing are reasonably expected by the data subject (we do not process data in ways that someone would not reasonably expect, which varies depending on the individual’s cognitive capability and understanding)
- There are legitimate legal grounds for collecting and processing data:
- Processing personal data shall be lawful only if one of the following applies:
- The data subject gives informed consent.
- Processing is required to fulfil a contractual obligation with the data subject.
- To comply with legal obligations as an employer; or as a data controller (for example, where we are required to disclose information about a data subject for law-enforcement purposes).
- There is legitimate interest and in situations where consent, contractual obligation, or legal obligation are not appropriate. Legitimate interest may only be used when specific criteria are met – the interests of the data controller need to be balanced against the interests of the data subjects – and must be decided via the legitimate interest assessment process.
Processing sensitive personal data shall be lawful if one of the following and additional bases apply (applicable to Re-engage):
- Explicit consent: freely given, specific, affirmative (opt-in) and unambiguous, and able to be withdrawn at any time. Explicit consent must be confirmed in a clear statement (whether oral or written), it must specify the nature of the special category data, and it should be separate from other consents.
- Employment, social security and social protection.
- Reasons of substantial public interest with a basis in law, particularly: Equality of opportunity or treatment, safeguarding of children and individuals at risk. Each condition legally requires a policy document if used (see appropriate policy documents (APD) for special category data).
- Archiving, research and statistics (with a basis in law).
Processed for limited purposes
Personal and sensitive data must only be used in ways that the person has knowingly given permission for. It is unacceptable to retrospectively assume consent to process their data in ways that the data subject has not knowingly given consent to.
Consent and explicit consent (for processing sensitive personal data) must be accurately recorded by the Charity (see obtaining oral consent). This includes recording contact methods and preferences and ensuring communications with individuals reflect their wishes (both permissive and restrictive), such as:
- specifically asking not to be contacted.
- requested that not being contacted in a specific way, either by informing us, or by registering with the Telephone Preference Service.
- has not given us specific consent, i.e., not opted-in, to further contact by email, text message, or telephone if they are on the Telephone Preference Service register.
Marketing communications
In relation to marketing and communications, the charity seeks and records affirmative consent before sending non-transactional communications (i.e., communications that are not strictly necessary to the provision of services to an individual). Consent must be knowingly and freely given, clear and specific. It must be explicit for Re-engage (not a partner organisation) and specify the types of communication to be used (for example, call, automated call, fax, email, text, letter). In particular:
- ‘Subscription’ to marketing communications must involve some form of very clear positive action – for example, ticking a box, clicking an icon, or sending an email – and the person must fully understand that they are giving consent to Re-engage (not a partner organisation).
- Re-engage cannot show consent if information about marketing is hidden as part of a privacy policy that is hard to find, difficult to understand, or rarely read.
- Re-engage may not rely on consent obtained indirectly (consent originally given to a third party). Valid consent must explicitly identify Re-engage and its public privacy policy. Generic consent covering any third party is not enough.
- Consent must be recorded accurately on Re-engage’s systems.
Data minimisation
Re-engage does not collect unnecessary data from individuals solely based on the assumption that it might be useful in the future.
Accurate and kept up to date
We take appropriate measures to record, update or rectify data in an accurate and timely manner. Inaccurate or outdated information about individuals must not be retained. Any delay in updating data – or reliance on outdated data – may cause undue distress or even harm to the data subject(s), especially if decisions are based on incorrect or outdated data.
Not kept longer than necessary for the purpose
Although legislation does not specify how long personal data may be retained, it is important that data not be retained longer than is required for the purpose it was originally collected, or as required by law or contract, or as permitted by consent. Only anonymised and disassociated data from an identifiable and living individual may be retained. Refer to the Retention Policy for more information.
Secure
All data is stored securely, whether in digital or hard copy format, while access to data is limited to those who require it. Access rights are periodically reviewed and revoked promptly when no longer necessary (for example, for leavers and colleagues changing roles). All staff and volunteers who access charity data undergo appropriate recruitment and vetting procedures and receive data protection training during their induction. Please refer to the Information security (InfoSec) policy for detailed information on how to keep data secure.
Important
Anyone becoming aware – or concerned for the possibility – of any information security incident or confidentiality breach involving personal or business confidential data must notify their line manager and the Data Protection Officer immediately.
Reportable incidents may include the theft or loss of a record or equipment, a deliberate attack on systems, sending personal information to the wrong address, unauthorised use of access to personal data by a member of staff, or technical failure.
Processed in line with the rights of data subjects
Data processing must be in accordance with legal rights of data subjects, who may without cost:
- Request access to any data about them (see Appendix A data subject requests).
- Prevent Re-engage using their data for direct-marketing purposes.
- Ask to have inaccurate data about them amended.
- Prevent processing that is likely to cause damage or distress to themselves or anyone else.
- Ask to have their data removed from Re-engage systems.
- Request all their personal data be transferred to other organisations’ systems.
Protected from transfer without adequate protection
People risk losing the protection of UK (or Crown Dependencies) data protection laws if their data is transferred to other organisations or outside the UK.
Transfer rules do not apply:
- Where the receiver is an employee of the sender, or the sender and receiver are part of the same legal entity, such as a company.
- Where the receiver is a UK service company under contract with Re-engage, even if the data flows from Re-engage to that service company’s processor which is located outside the uk. In that situation the restricted transfer may take place between the UK service company and its processor located outside the UK. But Re-engage must still undertake due diligence to understand global data flows and protections put in place.
Transfer rules apply where the receiver is a separate controller or processor and legally distinct from Re-engage. The receiver can be a separate sole trader, partnership, company, public authority, or other organisation, and includes separate companies in the same group. The lawfulness of 'restricted transfers' to other controllers, processors, or sub-processors depends on multiple conditions (see ICO guidance), but generally applies where Re-engage has initiated and agreed to transfer data.
Transfers of personal data are lawfully enabled by:
- Explicit consent from the data subject, or
- Recognised ‘adequacy regulations’ of other countries
- appropriate safeguards (including contractual assurance of adequate protection for the data subject’s rights)
- lawful exception.
Transfers of data must be assessed using the DPIA process (see Appendix B).
Appropriate policy documents (APD) for special category data
An appropriate policy document (APD) is a short document outlining compliance measures and retention policies for special category data. See guidance and template for APDs on the ICO website.
The Charity shall put in place an appropriate policy document (APD)s controlling special category data relating to employment, social security, and social protection law.
Employment, social security, and social protection
This condition is particularly relevant for employers when:
- checking if individuals are entitled to work in the UK.
- ensuring health, safety, and welfare of employees.
- maintaining records of statutory sick pay and maternity pay; or
- deducting trade union subscriptions from payroll.
This condition does not cover processing to meet purely contractual employment rights or obligations. The charity must be able to justify why processing of this specific data is ‘necessary’ - it must be a reasonable and proportionate way of meeting specific rights or obligations, and not collect or process more data than needed.
Regulating bodies
The charity shall register with regulatory authorities for data protection in particular but not limited to:
- Information Commissioner’s Office (ICO) of the United Kingdom.
- Jersey Office of the Information Commissioner (JOIC)
- Guernsey Office of the Data Protection Authority (ODPA)
- Isle of Man Information Commissioner's Office
In registering with regulating bodies, the charity will:
- Update regulators with the name of nominated or appointed Data Protection Officer(s)
- Notify and update all regulatory authorities on externally reportable issues relating to data protection and information security. See notification assessment tool provided by ICO.
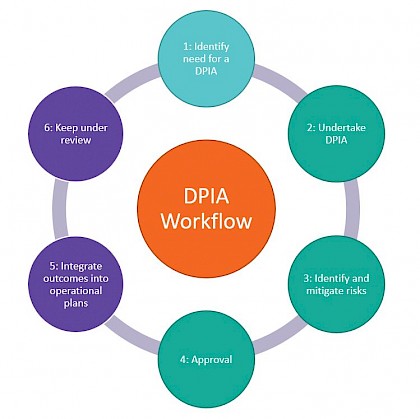
Data protection impact assessments (DPIAs)
Data Protection Impact Assessments (known as DPIAs) are a legally required process to identify and minimise the data protection risks of a project. Re-engage undertakes data protection impact assessments (DPIAs) for services, initiatives, and projects that expand data collection and processing to new information assets and systems. DPIAs are reviewed by IAOs and the DPO annually and as the scope or operational particulars of data collection and processing change. The DPO keeps DPIAs as a record of the charity’s general data processing. See data protection impact assessment process for further guidance.
Register of systems
Re-engage maintains a register of systems, which is a comprehensive account of information assets, systems, data collection and processing. The register of systems is reviewed at least annually by the DPO.
Data retention policy
The data retention policy outlines what data should/must be retained, for how long, and why.
Security
To observe the ‘security principle’ of data protection, please see our information security (InfoSec) policy
Public privacy policy and public cookie notice
As a data controller collecting and processing personal data, the Charity has in place a public privacy statement. The statement is available online, is easily accessed, and accessible to read by people whose data is collected by the charity. The notice describes:
- The processing of people’s personal data
- How long the data is retained
- Who the data is shared with
- A contact point at Re-engage for data protection
- Registration with governing bodies
- The public cookie notice is for visitors to Re-engage website(s), explaining that cookies are being used and what they do. If cookies are not strictly necessary to the running of a website, the user is given the option to consent or reject them.
The policy in summary
In general, you must:
- Seek advice if you are unclear about any aspect of data protection at Re-engage
- Stay alert and report suspicious activity, or any loss or suspected loss of data
- Destroy information properly when it is no longer needed
You must not:
- Engage in activity that causes risk – or results in harm to – to the security of Re-engage’s information systems and information the charity holds
- Undermine or seek to undermine the security of information systems
- Make copies of restricted charity information without permission
To protect your password, you must:
- Use hard-to-guess passwords that include different letter cases, numbers, and symbols (please refer to the InfoSec policy for password guidance)
- Change your password if you have suspicion that it may have been compromised
- Password-protect sensitive files and devices with strong passwords (please refer to the InfoSec policy for password guidance)
You must not:
- Disclose your password to anyone or allow others to use your login or password
- Write down your passwords or enter passwords in front of others.
- Reuse your Re-engage password as the password for any other service
To protect your email, you must:
- Be cautious of suspicious emails and links
- Pay attention for phishing traps in emails (for more detail about phishing, please refer to the InfoSec policy)
You must not:
- Open mail or attachments from an untrusted source
- Send restricted information by email unless it is encrypted and use the systems that you are told to use
To protect data and charity-issued devices such as laptops, tablets, and phones; you must:
- Lock devices when not in use by you
- Do not use open (unsecured) Wi-Fi hotspots or computers in internet cafes, public libraries etc
- Protect all devices with the latest security patches, anti-virus/anti-malware software and firewalls.
You must not:
- Leave your devices unlocked when left unattended
- Leave devices unattended in public
- Install unauthorised programs on your work devices (most installations need approval by the director of finance and resources)
- Lend your devices to any another person
- Use charity devices to store restricted information or use personal devices to store any charity related data
To protect charity systems and data, you must:
- Only access data you are allowed to and
- Only save data to locations where the charity is able to access it
- Access data remotely using approved cloud systems
You must not:
- Transfer data outside of approved systems (to a USB stick from example)
- Provide access to charity information or systems to those who are not entitled to access
- Leave hard copies of restricted information or devices unattended or unsecured
Appendix A: Data Protection processes at Re-engage
Obtaining oral consent
In relation to lawful bases for collecting and processing data, records of oral consent will demonstrate:
- When they consented: a note of the time and date which was made at the time of the conversation.
- What they were told (the script that was used) at the time.
- How they consented: a note of this should be made at the time of the conversation - it does not need to be a full record of the conversation.
Reporting incidents, data breaches, and concerns (requires implementation)
Data breaches relating to personal, sensitive, or confidential business data may put Re-engage or individuals (data subjects) at risk of fraud and identity theft. They may also cause significant distress to individuals and result in high costs and reputational damage to Re-engage.
Where there is a belief that information may have been lost, stolen, or compromised in any way - either deliberately or inadvertently - it must be immediately reported to the data protection officer in adherence with the process below. Failure to promptly report a breach can have a severe and lasting impact on the charity and may result in disciplinary action. General concerns about the way data is processed, or suspicions that data is held or used inappropriately, must be reported this straight away.
In the event of a data breach, the relevant person who discovers it will report the matter to the data protection officer, who will ensure that steps are taken:
- To limit any further damage.
- To recover any lost data.
- To assess the potential adverse consequences, including the risk to people’s rights and freedoms.
- To investigate the breach and identify any faults requiring remedial action.
- If appropriate, to notify the information commissioner’s office, unless satisfied that the breach is unlikely to result in a risk to the rights and freedoms of natural persons. Notification must be in accordance with article 33 of the GDPR (where feasible within 72 hours of its discovery). Further, GDPR art 33(5) requires the controller to document any personal data breaches.
Data subject requests
Subject access requests (SAR)
Individuals have the right to access their personal data and information about them. This is called a ‘subject access request’ and it is important that any request is responded to in a correct and timely way.
Subject access requests must be satisfied within a strict time frame of 40 calendar days. Failure to do so will place Re-engage in breach of legislation.
Subject access procedure:
- If the request is by phone, the caller is asked to put their request in writing (ensuring a formal record of the request)
- If there is any doubt as to whether the person requesting the data is the data subject themselves, consult the DPO.
- Pass any formal requests received in writing to the DPO.
Data rectification requests
Data protection law includes a right for individuals to have inaccurate personal data rectified, or completed if it is incomplete. An individual can make a request for rectification verbally or in writing. In certain circumstances you can refuse a request for rectification (see ICO guidance).
Data rectification requests must be responded to within one month.
Subject erasure requests
Data protection law introduces a right for individuals to have personal data erased (also known as the ‘right to be forgotten’). Individuals can make a request for erasure verbally or in writing.
The right is not absolute and only applies in certain circumstances (see ICO guidance).
Data erasure requests must be responded to within one month.
Appendix B: Data Protection management processes at Re-engage
Legitimate Interest Assessment (LIA) process
In relation to lawful bases for processing, legitimate interest is not focused on a particular purpose and therefore gives more scope to potentially rely on it in many different circumstances. It may be the most appropriate basis when:
- The processing is not required by law but is of a clear benefit to you or others.
- There is limited privacy impact on the individual.
- The individual should reasonably expect you to use their data in that way; and
- You cannot, or do not want to, give the individual full upfront control (i.e., consent) or bother them with disruptive consent requests when they are unlikely to object to the processing.
There is no obligation in data protection law to do a legitimate interest assessment (LIA), but it is best practice to conduct one and it is difficult to meet obligations under the accountability principle without it Conducting an LIA helps Re-engage ensure processing is lawful. See additional guidance and template documents on the ICO website.
Data protection impact assessment (DPIA) process
DPIAs are a legally required process to identify and minimise the data protection risks of a project. Re-engage undertakes DPIAs for any processing that is likely to result in a high risk to individuals, as well as some types of specified processing. It is also good practice to do a DPIA for any other major project which requires the processing of personal data. An effective DPIA can also bring broader compliance, financial, and reputational benefits and help to demonstrate accountability and building trust and engagement with individuals whose data is being processed.
A DPIA may cover a single processing operation or a group of similar processing operations. It may cover classes of data, such as ‘older people,’ or a service, such as ‘call companions’. But depending on the number of information systems processing that class of data (also known as an information asset), it may be easier to separate DPIAs into separate information systems.
In the event of an externally reportable event – such as a security breach – or a complaint, a catalogue of DPIAs help explain, evidence, and justify to regulators decisions about data collection, processing, risk, and transparency.